
Why you're not taking your online security seriously
This week, Opera announced they will be releasing a new version of their web browser with a couple of interesting features as standard. Opera is including free ad-blocking and a free VPN for all users. While both of these features are not entirely groundbreaking, what is new is including them by default, for every user.
This is all part of a rise in internet security for the average user, and it's been a long time coming. Since the beginning of web browsing, we’ve all been doing everything ‘in the clear’. This leaves us open to what is known as ‘man-in-the-middle’ attacks, where someone is listening in to everything we’re doing online.
Its more common than you might expect, and not just by "hackers". There’s a really good chance someone is listening in to what you are looking at right now; it could easily be your ISP, your employer, or even international governments, maybe even all of them depending on where in the world you are. I hope I'm going to convince you that encryption, and Internet security, shouldn’t be an afterthought, it ought to be an essential. While you may not think it, you do have something to hide - your bank details, your health history, your future career plans - there will always be some piece of information you might rather prefer it, if the whole world didn’t know.
Encryption can prevent this sort of intrusion from being possible. Encryption is the backbone of any network system, if we didn’t have it, most websites and Internet services just wouldn’t work. There have been some, frankly uninformed, nonsensical statements from international governments recently, talking about banning encryption online; if brought into law this would mean the end of any kind of personal transaction online, from banks and shops to Netflix and Facebook. Not just online services either, any business which has more than one location which needed to communicate, would have to either close their other locations, or start laying their own cables.
Imagine the Internet working a little like the Royal Mail. Whenever you send something over the internet unencrypted, it is like sending a postcard. Anyone in the system, at the post office, sorting office, or the guys delivering on foot, can read what you have written on the postcard. Thats fine if you’re just writing ‘wish you were here’, but you wouldn’t send your bank a postcard whenever you want to transfer money, or write your symptoms on a postcard and send them to your doctor.
Here’s the major difference in this analogy though, online, each person in the system your postcard passes through doesn’t have to spend the time to read through each postcard. They have the ability to scan the content for numbers that look like bank accounts, credit cards or login details, they can even locate personal photos and files whilst they are being transmitted.
Don’t believe the line that encryption is just for creeps and terrorists, it matters for you, too. To give an example of what information can be found, and how easy it is to get, I set up a system similar to one that is used on public WiFi network, to listen in to what’s passing though. I’m not a hacker, and I haven’t downloaded anything special or difficult to get hold of online by doing this. The software I’m using is something many network professionals have a legitimate use for and the setup took seconds.
I started browsing the web and within moments we can see where I’ve been. I visited Reddit, received an email from Krispy Kreme, checked Facebook, visited the NHS website, and finally logged into my Barclays Internet banking.
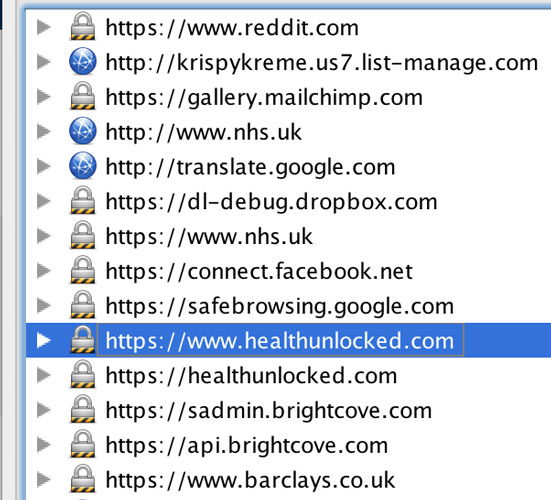
That visit to the NHS website looks interesting, lets look deeper…
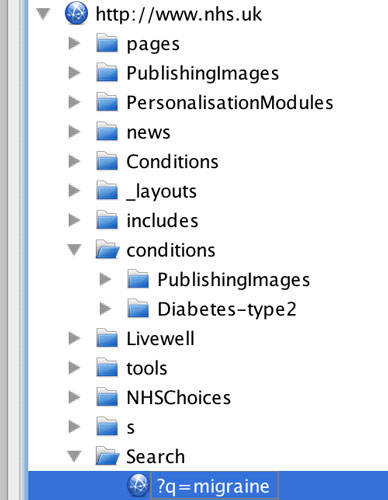
It seems I was reading up on Type 2 Diabetes, and I searched for Migraine. What if this was my work connection, and they found out about this? (Don’t worry Phil, I don’t have diabetes)
This is called “meta-data”. Even if your employer isn’t recording this, and there’s a good chance they are, the government wants to. The Investigatory Powers Bill currently being considered by parliament, will force ISPs to record this data for 12 months.
What about the data itself. This isn’t collected by the government, but can be collected by malicious actors - and not the Alan Rickman kind.
I logged into my private Photobucket account. All the albums I have in this account are set as private, therefore you would assume, it shouldn’t be accessible by anyone other than me. I uploaded a new photo, but through the available meta-data I was able to see the address to every photo in my account, and even what album they are in.
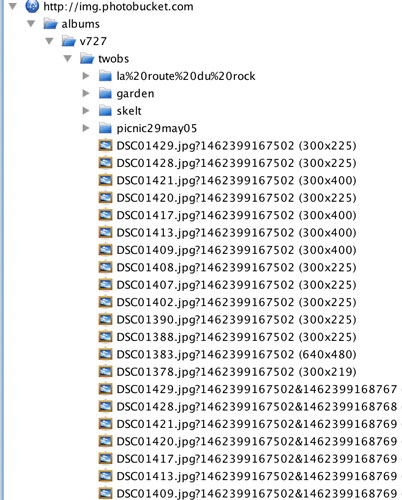
Checking the contents of the HTTP message (our ‘postcard’ from the Royal Mail analogy), I can even see the individual photos. Every kitten image I have in my private account (yes, I have a Phototbucket album full of kittens, who doesn’t?) is available to anyone monitoring web traffic through the network, without logging in. Good job its nothing more personal than kittens, eh?
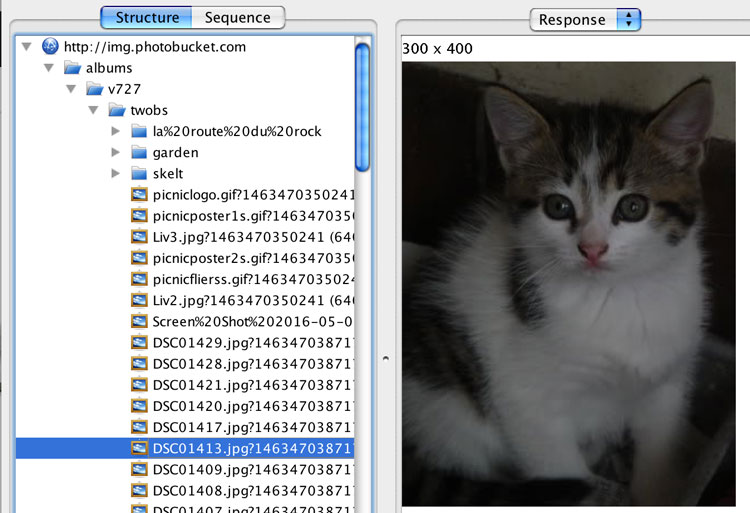
Then Apple Mail decides to update my inbox, it sends a bunch of requests to the mail provider. A quick flick through shows me the most worrying piece of information of them all. My full email login details, including the password.
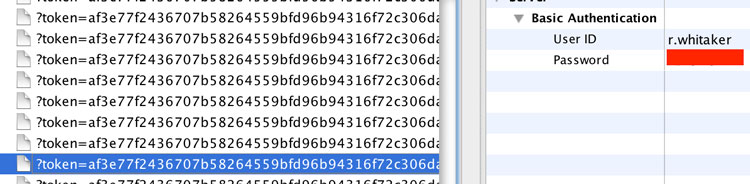
Access to an email account is the “Holy Grail” for a malicious online attacker. All your other accounts are often linked to it. With access to an email address, an attacker can change almost any password to online accounts you may have linked with your email address and it is easy to see what companies you deal with, in what way, and when. Maybe they can see your pay slips if they are emailed to you? If not, there’s a good chance you’ve sent your bank details to someone via email at some point. Even if you didn’t, they’ll possibly be able to look through and see see who you bank with, and whilst they are there, they may even be able to gather all the personal information they’ll need to get access to your bank or other accounts - your date of birth, personal history, and more are often in peoples emails.
Hopefully by now, I’ve convinced you that internet security is an essential service for everybody, and for every device you use. I’m not talking about buying Norton bloatware, either. There’s no way to completely prevent attacks like this happening, but nothing is better than being careful. With a few small changes, which won’t affect the way you access the Internet, and (mostly) won’t cost anything you can make yourself a lot less of an easy target.
1. Use a good ad-blocker
uBlock, or uBlock Origin is currently the best option. Adblock Plus, the market leader, is unfortunately unreliable as they accept payments to prevent blocking certain items. An ad blocker will help to prevent malicious code from other websites appearing in the sites you visit. The sort of code included in ads is used to track you, thats well known, but it can at times be used to steal login credentials or install malicious software on your device.
2. Use HTTPS Everywhere
HTTPS Everywhere is provided for free by EFF, again unfortunately not available for Safari. HTTPS encrypts the requests (‘postcards’, as in our earlier analogy again) your browser makes, and turns them more into ‘envelopes’ - meaning the places they pass though can see where its heading, but not what is in it. Unfortunately, this relies on the websites you are visiting supporting HTTPS, but most support this these days. This doesn’t make you immune to the sort of attack I demonstrated above, but it certainly helps.
3. Use a paid VPN
A VPN encrypts every request that comes in and out of your device, and at the same time, re-routes them. This fortunately doesn’t rely on the website supporting it, but the encryption isn’t end-to-end. What comes out at the other end of the VPN “pipe” is still a ‘postcard’ but the so-called “man-in-the-middle” who is trying to snoop on your data, can’t tell that its been sent from, or being sent to, you. There are several free VPN services available, but I’d advise you against these. The services being offered for free will often inject ads into your browsing, or sell your browsing habits to advertisers to support the “free” software. There is an often used refrain that where you are not paying for a service, you are the product, meaning simply, your information is used and sold by the company whose service you are using. I personally use TunnelBear, which costs c$6.99 a month, approximately £4 depending on the exchange rate.
4. If you’re using public WiFi, be extra secure
If you’re using a wifi connection you didn’t set up yourself, don’t use it to do anything personal, confidential or sensitive. Its best to assume that whilst on these kinds of connections, that your network traffic is being watched. These connections could be easily compromised by another user on the network exactly the way I demonstrated earlier. Some public WiFi providers even track what sites you visit to sell to advertisers.
These four steps are a great start to more secure web browsing, and you don’t need any specialist knowledge to get them installed and begin protecting yourself whilst you use the web. However, if I’ve wetted your appetite and you want to find out more, the EFF have some great advice on personal privacy online, and if you like the occasional meme and love Taylor Swift, why not get her advice on security, too.
Follow us on Twitter.
Email us at info@krcs.co.uk
Call us on 0115 9851797
 12 months interest free on any Mac over £1,000.
12 months interest free on any Mac over £1,000.
No Comments yet. be the first to comment.